|
|
Pentagram Technologies Maintained Under Section 59 of the Indian Partnership Firm Act, 1932 |
|||||||
|
An Indian Partnership company incorporated at Hyderabad, India in February 11, 2022 Previously known as Pentagram Research Centre Private Limited incorporated in February 27, 1997 |
||||||||
|
Mission: Better Technology Through Better Research |
||||||||
|
Home | People | Departments | Products | Projects | Publications | Research | Journal | Conference | Alliance | Contact |
||||||||
|
|
|
|||||||
|
The company proposes five major projects of both national importance and commercial viability and five other projects of absolute commercial viability. All ten projects would ensure considerable return on investment. |
||||||||
|
Security Projects of National Importance Proposed by the Company All techniques suggested for executing these projects have been developed in-house and kept as strictly confidential intellectual property of the company, which could be shared with those organizations interested in executing these projects. |
||||||||
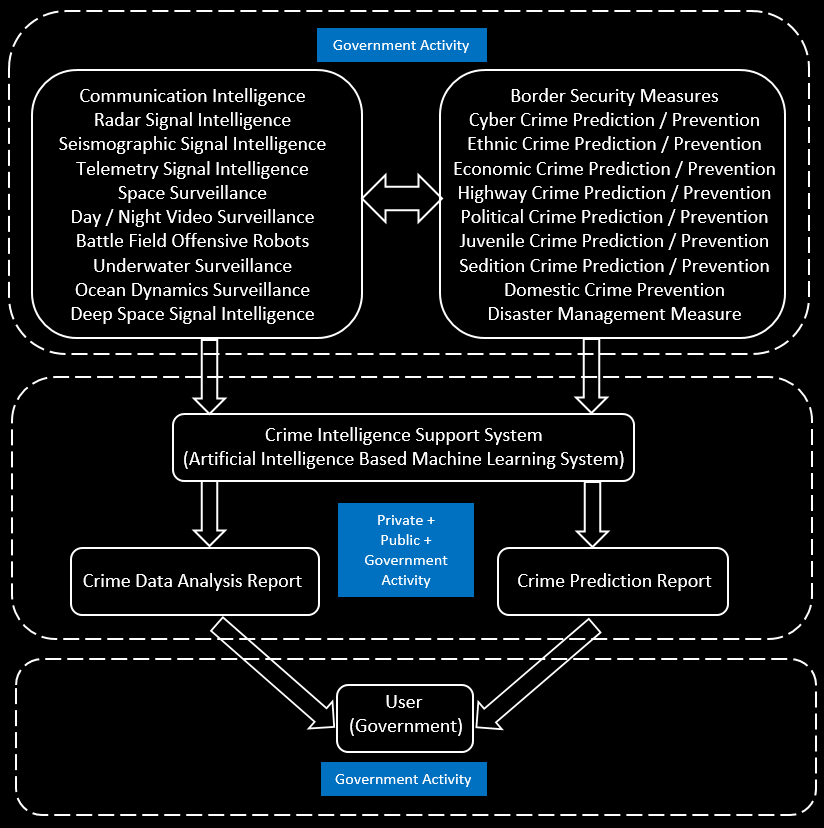
| Crime Intelligence Support System (CISS) | ||||||||
|
||||||||
|
Pentagram Technologies is a large team of highly qualified and self motivated international scientists and technologists working ''without any support'' on the possibility of developing an integrated Criminal Intelligence Support System involving various security activities like Electronic Support Measures. With ample support from interested companies, we would be able to realize the dream project which would enable security agencies to ensure crime free zones and nations. To begin with, Pentagram Research is developing, in association with Zone Technologies and Helios & Matheson Analytics Inc., USA, a preliminary version called 'Crime Prediction Support System (CPSS)” which would network people, various government and private security agencies, emergency units and media with the idea of creating a safe and happy world. |
||||||||
|
Coastal Surveillance Support System (CSSS) |
||||||||
 Indian peninsula has a long coast line of 7516.6 km which is susceptible for infiltration by terrorists and illegal immigrants. The mainland of India has 5422.6 km coast line and the island territories 2094 km. This long coast line has to be under constant surveillance in order to detect illegal entry by terrorists and illegal immigrants. In order to achieve this, a three tier surveillance strategy could be adopted by erecting an electromagnetic fencing, laser / optical fencing and underwater surveillance by unmanned submarines. All the sensors to be used for this purpose would be IP enabled and this setup along with a secretive operational semantics would invoke a net-centric command and control defense strategy. The term ‘Command and Control (C2)’ denotes a set of organizational and technical attributes and processes by which an approved organization marshals and employs human, physical, and information resources to solve problems and accomplish missions of nation’s security interest. As on date, most of the monitoring stations for communication and radar intelligence are functional in the northern sector of the country, a few in the western sector and a few in the north eastern frontier sector for daily intercept and reporting. Very few are functional in the southern sector. Most of the mission flights are carried out in the western and northern sector and Electronic Order of Battle records prepared and submitted to the Joint Intelligence Committee depending on the needs and requirement of the government. What is missing in India is unmanned “Coast Line Radar Fencing”, “Coast Line Video Surveillance” and “Underwater Surveillance”. The entire operational mechanism is referred to as ‘Uninterrupted Coastal Surveillance’. Ineffective approach or complete absence of such an operational mechanism would indeed lead to serious security threat to the integrity and sovereignty of the country and the general public would have to face the after effects of intrusion by radicals, terrorists and illegal migrants. This is a serious security problem faced by India today. Project CSSS is an end-to-end solution suggested to the government of India to counter all kinds of intrusion and insurgence through coastal line that might cause breach of security and heavy loss of life and national property. A consortium of companies, individual experts and government officials could be identified, security cleared and empowered to plan, procure and erect Monitoring Stations (MS) at strategic places throughout the coast line. A ground based MS is a radar unit associated with a laser transmitter / receiver and a video surveillance system consisting of both optical and thermal imaging sensors. All sensors would be IP enabled. In addition to installing MS at various places on the shore, the consortium would identify and procure unmanned submarines and catamarans to be positioned at strategic places well within the territorial waters throughout the coast line. Each MS would control a group of unmanned submarines, catamarans and flying drones. Data collected from various sensors would be treated as an ensemble using multi sensor fusion techniques and presented for data analysis. The data ensemble due to CSSS would be fed to a machine learning cognitive engine which is a three dimensional artificial intelligence based neural network. In addition, satellite image data, Crime Intelligence Support System (CISS) data, ELINT data, COMINT data, Seismographic Intelligence data, public media intelligence data would be used as collateral information in the prediction process of the cognitive engine. |
||||||||
|
Coastal Surveillance Support System (CSSS) - The Project
|
||||||||
|
Pentagram Technologies is a large team of highly qualified and self motivated international scientists and technologists working ''without any support'' on the possibility of developing an integrated Coastal Surveillance Support System involving various security activities like Electronic Support Measures. With ample support from interested companies, we would be able to realize the dream project which would enable security agencies to ensure safe and secured zones free from infiltration, terrorism and subsequent radicalization. |
||||||||
|
Radar Intelligence Support System (RISS) |
|
|
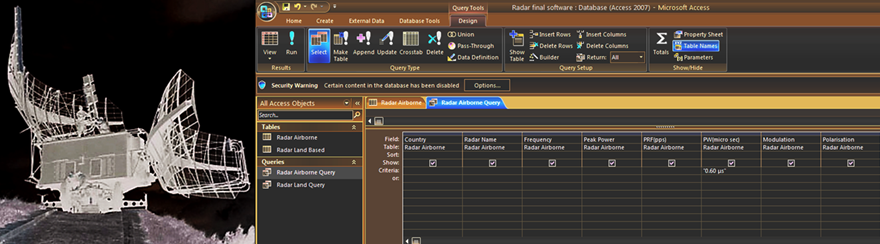
Pentagram Technologies would be able to provide various technical support to the organizations involved in the state-of-the-art of ELINT. ELINT (Electronic Intelligence) planes equipped with EW capabilities are normally flown along the border or over the enemy territories to intercept and store data aboard the aircraft. Many such missions are carried out to gather as much data as possible. Larger the amount of data collected better is the accuracy of the parameters extracted from the data. This proposal is concerned with techniques and software tools to be used in off-line analysis and extraction of radar parameters from data intercepted and recorded during Electronic Intelligence (ELINT) mission flights. The techniques proposed are unique and they use traditional methods and equipment that will help enable the EW operators to quickly do the analysis and make the threat assessment for use in current and future combat. |
|
Radar Intelligence Support System (RISS) - The Project
|
|
|
|
|
Pentagram Technologies is a large team of highly qualified and self motivated international scientists and technologists working ''without any support'' on the possibility of developing a radar portal which could be used by authenticated persons to get complete technical specifications of various radars and other warfare equipment and details of their manufacturers. Authenticated ESM operators can use the portal for mapping and emitter location purposes real time on board. Academicians can freely use part of this portal for getting technical details pertaining to various systems and associated signal processing capabilities with research perspective. |
||
| Video Surveillance Support System (VSSS) |
|
Video Surveillance Support System (VSSS) - The Project
|
|
|
|
|
|
|
| Pentagram Technologies is a large team of highly qualified and self motivated international scientists and technologists working ''without any support'' on the possibility of developing an Artificial Intelligence (AI) based, net centric day and night video surveillance security cover for the entire country. This facility could also be extended to border security and coastal surveillance. The term 'surveillance' not only refers to visual monitoring of areas of interest but also tracking targets of special interest. | |||


 ESM
system is designed to accomplish as quickly as possible the
following tasks: Intercept a transmitted signal at any frequency,
Determine the type of modulation in the signal, Identify the usable
intelligence carried in the signal, Measure the direction of arrival
of the waveform for calculations that locate the transmitter,
Process and record the signal characteristics, Display to the
operator and transfer to the computer for decision making. In short,
the ESM system must gather, process, and display all signals of
interest. Radar receivers along with certain additional equipment
form the intercept system. They are of three types: Airborne
intercept system, Ground based intercept system and Truck mounted
intercept system. Airborne intercept system is used during special
mission flights meant for short duration intelligence activity.
Ground based intercept syste m is used by round the clock monitoring
stations located at strategic places. Truck mounted intercept system
is used by the ESM section of a radar regiment or by the
intelligence units of air force, army and navy. Special mission
flights are arranged in such a way that the surveillance aircraft
flies along the border. Based on the predetermined flight plan, the
pilot would fly the aircraft. The ESM equipment would be powered on
during the entire flight. Based on the briefing given to the ESM
operators, they would tune the receivers and the received radio
frequencies (RF) would be detected, pulse stretched and recorded in
a low speed (7.5 ips) airborne tape recorder. Wide band receivers
would constantly receive radio frequencies which are detected, pulse
stretched and recorded in various tracks of the tape. In addition,
time code is also recorded continuously.
ESM
system is designed to accomplish as quickly as possible the
following tasks: Intercept a transmitted signal at any frequency,
Determine the type of modulation in the signal, Identify the usable
intelligence carried in the signal, Measure the direction of arrival
of the waveform for calculations that locate the transmitter,
Process and record the signal characteristics, Display to the
operator and transfer to the computer for decision making. In short,
the ESM system must gather, process, and display all signals of
interest. Radar receivers along with certain additional equipment
form the intercept system. They are of three types: Airborne
intercept system, Ground based intercept system and Truck mounted
intercept system. Airborne intercept system is used during special
mission flights meant for short duration intelligence activity.
Ground based intercept syste m is used by round the clock monitoring
stations located at strategic places. Truck mounted intercept system
is used by the ESM section of a radar regiment or by the
intelligence units of air force, army and navy. Special mission
flights are arranged in such a way that the surveillance aircraft
flies along the border. Based on the predetermined flight plan, the
pilot would fly the aircraft. The ESM equipment would be powered on
during the entire flight. Based on the briefing given to the ESM
operators, they would tune the receivers and the received radio
frequencies (RF) would be detected, pulse stretched and recorded in
a low speed (7.5 ips) airborne tape recorder. Wide band receivers
would constantly receive radio frequencies which are detected, pulse
stretched and recorded in various tracks of the tape. In addition,
time code is also recorded continuously.  Magnetic
tapes are obtained after a mission flight, off-line analysis
is carried out and analysis report prepared by the signal
analyst. Then the analysts, pilots and mission operatives
jointly prepare the radar signal intelligence maps. Figure
shown here is a model radar signal processing booth
consisting of magnetic tape recorder/ reproducer, time code
generator/ reader, spectrum analyzer, multi beam multi trace
oscilloscope, frequency counter, PRF synthesizer, and other
ancillary equipment..To make strategic decisions, the
department of defense relies mainly on intelligence
regarding the area of operations and the enemy. Obtaining
information about enemy is the most difficult task.
Information and intelligence about enemy force are referred
to as ‘Order of Battle’ (OB). It should be noted that OB not
only refers to intelligence about military forces of enemies
or potential enemies, but also to that about friendly and
neutral forces. Hence, OB is all about the identification of
personnel, units, and equipment. OB is collected both in
peacetime and wartime. During peacetime, OB is mainly
concerned with collecting strategic intelligence. During
wartime, OB is treated both as strategic intelligence and
also as a part of tactical intelligence analysis. In the
present context, EOB is all about the intelligence collected
as part of ESM activity, system functionalities, MTBF and
other capabilities of the radar, and about the radar
regiment and its movement. All these amount to saying that
EOB plays a significant role in peace time strategic
planning. From intelligence data collected by the ESM staff,
operational staff compiles a likely order of battle by
assessing the following factors: Enemy's Composition,
Disposition, Strength. Composition is about the command
structure and organization of headquarters and subunits.
Disposition: refers to geographical locations of unit
headquarters and subunits. Strength is expressed in units
and weight of fire delivered by its weapon systems. Enemy
capabilities and limitations are Personnel training,
Logistics as to how the enemy unit obtains its supplies and
lines of communication, Combat Effectiveness using complex
algorithms and combat modeling applications and Electronic
Technical Data used to provide data for the combat modeling
applications. Enemy's Most Likely Course of Action are
Tactics used by the enemy unit., Miscellaneous data related
to specific task, mission or operations and known enemy
personnel.
Magnetic
tapes are obtained after a mission flight, off-line analysis
is carried out and analysis report prepared by the signal
analyst. Then the analysts, pilots and mission operatives
jointly prepare the radar signal intelligence maps. Figure
shown here is a model radar signal processing booth
consisting of magnetic tape recorder/ reproducer, time code
generator/ reader, spectrum analyzer, multi beam multi trace
oscilloscope, frequency counter, PRF synthesizer, and other
ancillary equipment..To make strategic decisions, the
department of defense relies mainly on intelligence
regarding the area of operations and the enemy. Obtaining
information about enemy is the most difficult task.
Information and intelligence about enemy force are referred
to as ‘Order of Battle’ (OB). It should be noted that OB not
only refers to intelligence about military forces of enemies
or potential enemies, but also to that about friendly and
neutral forces. Hence, OB is all about the identification of
personnel, units, and equipment. OB is collected both in
peacetime and wartime. During peacetime, OB is mainly
concerned with collecting strategic intelligence. During
wartime, OB is treated both as strategic intelligence and
also as a part of tactical intelligence analysis. In the
present context, EOB is all about the intelligence collected
as part of ESM activity, system functionalities, MTBF and
other capabilities of the radar, and about the radar
regiment and its movement. All these amount to saying that
EOB plays a significant role in peace time strategic
planning. From intelligence data collected by the ESM staff,
operational staff compiles a likely order of battle by
assessing the following factors: Enemy's Composition,
Disposition, Strength. Composition is about the command
structure and organization of headquarters and subunits.
Disposition: refers to geographical locations of unit
headquarters and subunits. Strength is expressed in units
and weight of fire delivered by its weapon systems. Enemy
capabilities and limitations are Personnel training,
Logistics as to how the enemy unit obtains its supplies and
lines of communication, Combat Effectiveness using complex
algorithms and combat modeling applications and Electronic
Technical Data used to provide data for the combat modeling
applications. Enemy's Most Likely Course of Action are
Tactics used by the enemy unit., Miscellaneous data related
to specific task, mission or operations and known enemy
personnel.